Blind to your search results? Your reputation is already at risk.
Online search results shape your reputation — whether you're an individual or a business. One negative article, forum thread, or review can cost you trust, opportunities, or revenue. That’s why we built an always-on, automated solution to monitor every inch of the search landscape for harmful content.
Take back control→Malala Leides


Phil Graham


William Brown


Alex Hormozi


Ahmed Ben Chaibah


Alan Graves


Alex Fedotoff


Laurence Thomas


Malala Leides


Phil Graham


William Brown


Alex Hormozi


Ahmed Ben Chaibah


Alan Graves


Alex Fedotoff


Laurence Thomas


Why do harmful search results matter?
Search engines are the first place people go when they hear your name. A single piece of negative content can: 📉 Appear above your website and push down your negative content. 💸 Lead to lost sales, failed job interviews, or missed investor deals. 📢 Get amplified by social media, making it difficult to control the narrative. You don't get a second chance at a first impression. This is your early warning system.
Get Started→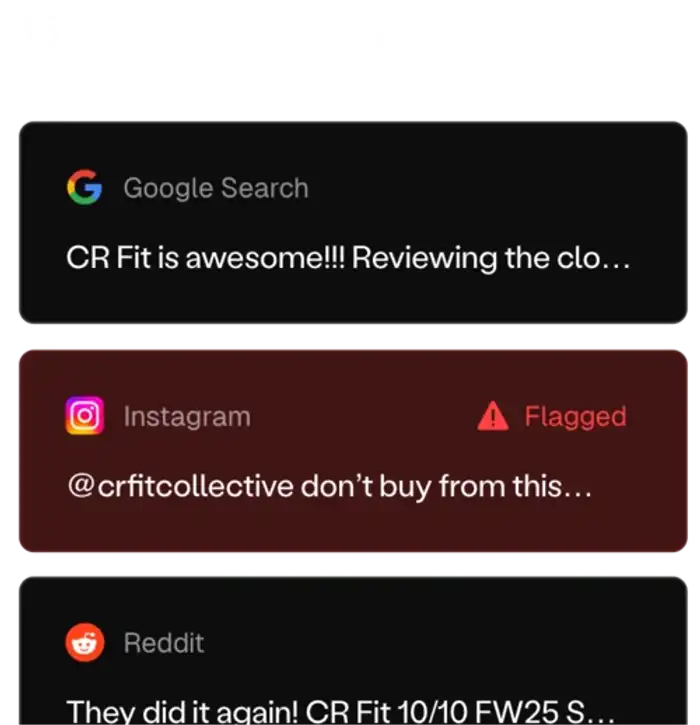
We monitor across all major platforms
ContentRemoval monitors quietly in the background. No setup needed. Just tell us what names, brands, or keywords to track — we do the rest.
Get Started→

Bing

Yahoo

DuckDuckGo

Baidu




X/Twitter

Blogger


Bing

Yahoo

DuckDuckGo

Baidu




X/Twitter

Blogger


Bing

Yahoo

DuckDuckGo

Baidu




X/Twitter

Blogger


Bing

Yahoo

DuckDuckGo

Baidu




X/Twitter

Blogger
Manual monitoring simply doesn't work.
We automate the entire monitoring process with intelligent tracking and real-time alerts, so you never miss a threat again. We don’t just scan results - we extract, timestamp, and alert you instantly when damaging content surfaces.
We fix that→Doing this yourself? Here’s why it fails:
Constant Updates
🔄
Search results change constantly - new results appear daily.
Too Many Platforms
🌐
You can't check every platform, every day - there are too many.
Complex Algorithms
🕵️
Search engines tailor results by device, location, and history, so manual results are incomplete.
No Alerts
🔕
You'll only notice something’s wrong when it’s already caused damage.
No Audit Trail
📋
Manual methods don’t log when or where results changed.
Time-Consuming
⏱️
Hours spent searching for limited results should be better invested elsewhere.
Private. Accurate. Always On.
Reputation damage happens silently and fast. By the time you discover it, the harm is already done. Monitoring is your first line of defense.
Get Started→Real-time Alerts
🔔
Summary Reports
📊
Full Search Results History
🗄️
Secure Access
🔒
Enterprise-ready
🏢
And so much more...
🛡️
Get started in 2 minutes
No complex tools. No bloated dashboards. Just clear insights when and where it matters.
Get Started→Defamation
Hate Speech
Copyright Infringement
Trademark Infringement
Personal Data
Cyber Abuse
Revenge Porn
Legal Proceedings
Outdated Content
Identity Theft
Privacy Violations
Harassment
Impersonation
Doxxing
Explicit Content
Cyberstalking
Competitor Attacks
Digital Products
Unauthorized Use
Defamation
Hate Speech
Copyright Infringement
Trademark Infringement
Personal Data
Cyber Abuse
Revenge Porn
Legal Proceedings
Outdated Content
Identity Theft
Privacy Violations
Harassment
Impersonation
Doxxing
Explicit Content
Cyberstalking
Competitor Attacks
Digital Products
Unauthorized Use
Defamation
Hate Speech
Copyright Infringement
Trademark Infringement
Personal Data
Cyber Abuse
Revenge Porn
Legal Proceedings
Outdated Content
Identity Theft
Privacy Violations
Harassment
Impersonation
Doxxing
Explicit Content
Cyberstalking
Competitor Attacks
Digital Products
Unauthorized Use
Defamation
Hate Speech
Copyright Infringement
Trademark Infringement
Personal Data
Cyber Abuse
Revenge Porn
Legal Proceedings
Outdated Content
Identity Theft
Privacy Violations
Harassment
Impersonation
Doxxing
Explicit Content
Cyberstalking
Competitor Attacks
Digital Products
Unauthorized Use
Defamation
Hate Speech
Copyright Infringement
Trademark Infringement
Personal Data
Cyber Abuse
Revenge Porn
Legal Proceedings
Outdated Content
Identity Theft
Privacy Violations
Harassment
Impersonation
Doxxing
Explicit Content
Cyberstalking
Competitor Attacks
Digital Products
Unauthorized Use
Defamation
Hate Speech
Copyright Infringement
Trademark Infringement
Personal Data
Cyber Abuse
Revenge Porn
Legal Proceedings
Outdated Content
Identity Theft
Privacy Violations
Harassment
Impersonation
Doxxing
Explicit Content
Cyberstalking
Competitor Attacks
Digital Products
Unauthorized Use
 Google
Google Yahoo
Yahoo Bing
Bing DuckDuckGo
DuckDuckGo Baidu
Baidu Instagram
Instagram Facebook
Facebook Reddit
Reddit X / Twitter
X / Twitter Blogger
Blogger YouTube
YouTube TikTok
TikTok Pinterest
Pinterest LinkedIn
LinkedIn Vimeo
Vimeo Tumblr
Tumblr Alex Hormozi
Alex Hormozi Sweat.com
Sweat.com Saski Collection
Saski Collection Defamation
Defamation Revenge Porn
Revenge Porn