Remove Content from X / Twitter
Quickly identify and remove harmful posts, mentions, and media from X/Twitter, protecting your online presence on one of the world's most influential platforms.
Get Started→@alexfontaine

Malala Leides


Phil Graham


William Brown


Alex Hormozi


Ahmed Ben Chaibah


Alan Graves


Alex Fedotoff


Laurence Thomas


Malala Leides


Phil Graham


William Brown


Alex Hormozi


Ahmed Ben Chaibah


Alan Graves


Alex Fedotoff


Laurence Thomas


650 million
people use X/Twitter every month
As the world's leading real-time discussion platform, damaging content on X / Twitter spreads virally within minutes through retweets, quotes, and replies, reaching massive global audiences instantly. With its powerful search and trending algorithms, negative tweets remain highly visible and can resurface repeatedly, while AI tools like Grok analyze and amplify content's reach. While positive engagement can rapidly build influence, even a single harmful tweet can cascade across networks and destroy what has taken years to build.
Remove X/Twitter content now→Need To Remove Content On X / Twitter?
Companies disregard applicants, customers avoid brands, and relationships can end over posts on shared via X. If there is something distressing you on X, use ContentRemoval to help remove it fast.
Get Started→Damaging Tweets
Remove damaging tweets that have gained widespread attention through retweets and quotes. Stop the spread of harmful content before it reaches an even larger audience.
Fake Accounts
Eliminate impersonator accounts, parody profiles, or fraudulent pages targeting your identity. Prevent scammers and bad actors from damaging your authentic presence.
Unwanted Media
Remove unauthorized photos, videos, or memes that harm your reputation. Address visual content that's been manipulated, taken out of context, or shared without permission.
Harmful Threads
Combat lengthy discussion threads and reply chains that damage your reputation. Take control of conversations that spiral into targeted harassment or abuse.
Been there, done that.
From CEOs to celebrities to everyday people, we handle the worst of the internet. Your impossible is our everyday.
Get Started→These fake accounts not only diluted my brand presence but also risked misleading my vast follower base with counterfeit information.
How Alex Hormozi Stopped Fake Accounts Scamming His Customers
Protect your online presence, on all platforms, forever.
Get Started→Monitor the internet
Expertly flag negative content
Reveal hidden content sources
Deploy strategic removal requests
Track removal progress
Monitoring
Continuously scan search engines, social media, & more with real-time detection.

Detection
Quickly flag negative content with advanced AI detection and customizable filters.
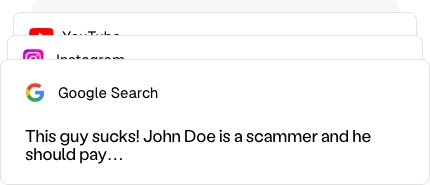
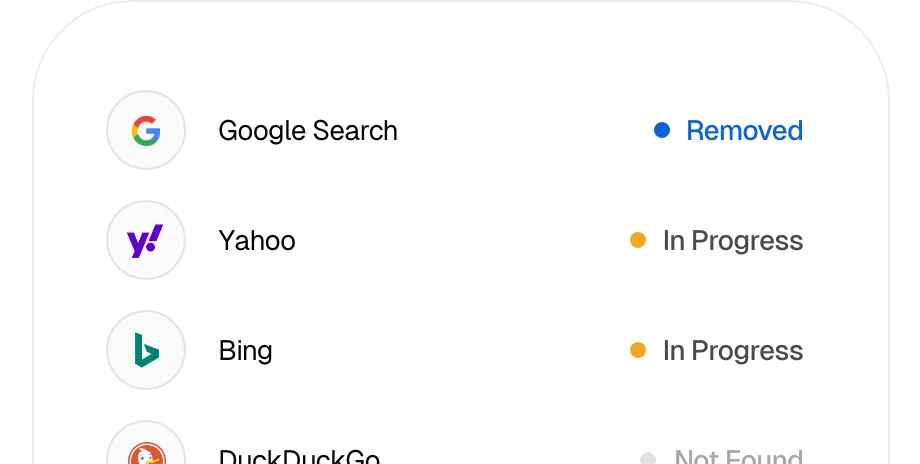
Google Search
Is John Doe a Scam? Uncovering the Truth Behind the Allegations
YouTube
SHOCKING! Leaked Messages of John Doe Exposed - You Won't Believe This!
Bing
John Doe's Scandal: What the Latest Investigations Reveal
Google Search
Is John Doe a Scam? Uncovering the Truth Behind the Allegations
YouTube
SHOCKING! Leaked Messages of John Doe Exposed - You Won't Believe This!
Bing
John Doe's Scandal: What the Latest Investigations Reveal
Google Search
The Dark Side of John Doe: New Evidence of Fraudulent Activities
Yahoo
Public Outrage: The Shocking Truth About John Doe's Alleged Scams
YouTube
EXCLUSIVE: Watch the Leaked Footage of John Doe's Controversial Actions!
Google Search
The Dark Side of John Doe: New Evidence of Fraudulent Activities
Yahoo
Public Outrage: The Shocking Truth About John Doe's Alleged Scams
YouTube
EXCLUSIVE: Watch the Leaked Footage of John Doe's Controversial Actions!
Tracing
Trace content origins to pinpoint the real sources of harmful content.
Removal
Send targeted requests with proven removal strategies.
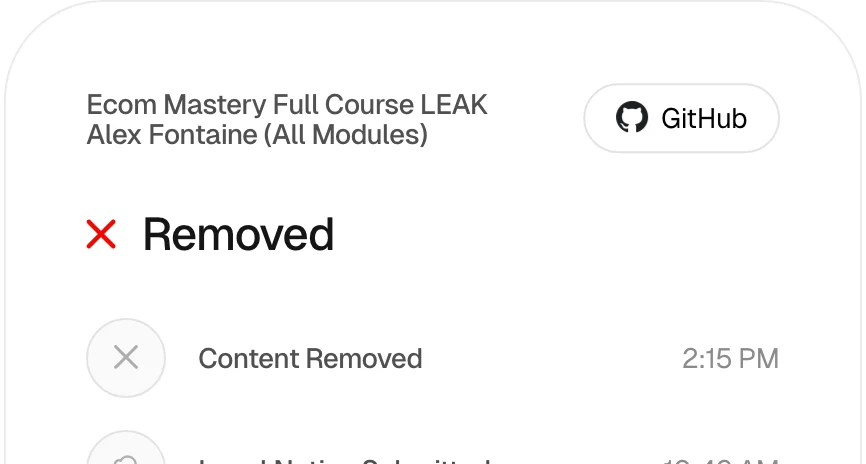
Alex Fontaine (All Modules)


Tracking
Monitor removal status across every platform and provider.
Whatever you're trying to remove, we've got your back
Defamation
Hate Speech
Copyright Infringement
Trademark Infringement
Personal Data
Cyber Abuse
Revenge Porn
Legal Proceedings
Outdated Content
Identity Theft
Privacy Violations
Harassment
Impersonation
Doxxing
Explicit Content
Cyberstalking
Competitor Attacks
Digital Products
Unauthorized Use
Defamation
Hate Speech
Copyright Infringement
Trademark Infringement
Personal Data
Cyber Abuse
Revenge Porn
Legal Proceedings
Outdated Content
Identity Theft
Privacy Violations
Harassment
Impersonation
Doxxing
Explicit Content
Cyberstalking
Competitor Attacks
Digital Products
Unauthorized Use
Defamation
Hate Speech
Copyright Infringement
Trademark Infringement
Personal Data
Cyber Abuse
Revenge Porn
Legal Proceedings
Outdated Content
Identity Theft
Privacy Violations
Harassment
Impersonation
Doxxing
Explicit Content
Cyberstalking
Competitor Attacks
Digital Products
Unauthorized Use
Defamation
Hate Speech
Copyright Infringement
Trademark Infringement
Personal Data
Cyber Abuse
Revenge Porn
Legal Proceedings
Outdated Content
Identity Theft
Privacy Violations
Harassment
Impersonation
Doxxing
Explicit Content
Cyberstalking
Competitor Attacks
Digital Products
Unauthorized Use
Defamation
Hate Speech
Copyright Infringement
Trademark Infringement
Personal Data
Cyber Abuse
Revenge Porn
Legal Proceedings
Outdated Content
Identity Theft
Privacy Violations
Harassment
Impersonation
Doxxing
Explicit Content
Cyberstalking
Competitor Attacks
Digital Products
Unauthorized Use
Defamation
Hate Speech
Copyright Infringement
Trademark Infringement
Personal Data
Cyber Abuse
Revenge Porn
Legal Proceedings
Outdated Content
Identity Theft
Privacy Violations
Harassment
Impersonation
Doxxing
Explicit Content
Cyberstalking
Competitor Attacks
Digital Products
Unauthorized Use
 Google
Google Yahoo
Yahoo Bing
Bing DuckDuckGo
DuckDuckGo Baidu
Baidu Instagram
Instagram Facebook
Facebook Reddit
Reddit X / Twitter
X / Twitter Blogger
Blogger YouTube
YouTube TikTok
TikTok Pinterest
Pinterest LinkedIn
LinkedIn Vimeo
Vimeo Tumblr
Tumblr Alex Hormozi
Alex Hormozi Sweat.com
Sweat.com Saski Collection
Saski Collection Defamation
Defamation Revenge Porn
Revenge Porn